Implementing crypto authentication in accessories and disposables
Author: Nicolas Demoulin, EMEA Marketing Manager, Secure Products Group, Microchip Technology
The need for crypto authentication
As consumers, we become adept at learning the relative merits of a brand, whether for a car, a power tool or simply a can of soup. Companies invest lots of money to establish, develop and maintain their brand credentials so that, as consumers, we choose what we believe is a valued brand. The exact reasons for our brand preferences vary, ranging from wishing to embrace the brand's lifestyle to more practical reasons of quality, durability and value for money. It's not just consumer product manufacturers that build their brands. Brand identity applies to industrial, commercial and medical products too. Marketing professionals are experts in communicating and reinforcing brand values in everything they do and will take active steps to protect their brand at all costs. A brand's equity extends to reputation, trust and social values, for which the firm's logo becomes globally recognized. Attempts by other companies to copy or impersonate the logo or brand promise receive prompt attention.
Apart from the marketing aspects of a brand, the company's products and services need protection too. In global markets, counterfeiting has become a significant issue. Everything from power tool battery packs, electronic components, e-cigarettes, printer cartridges and medical equipment accessories is copied by unscrupulous counterfeiters.
Today, product manufacturers use crypto authentication techniques to protect customers from counterfeit products. Figure 1 highlights the many factors for implementing crypto authentication techniques.
Perhaps one of the first use cases of crypto authentication was for the batteries of portable power tools. Consumers soon found that counterfeit products looked just like the proper manufacturer's battery but didn't last as long, became faulty and placed the user at risk of the tool catching fire. Crypto authentication suits any product with an embedded system and is ideal for those with replaceable, interchangeable accessories or disposable consumables.
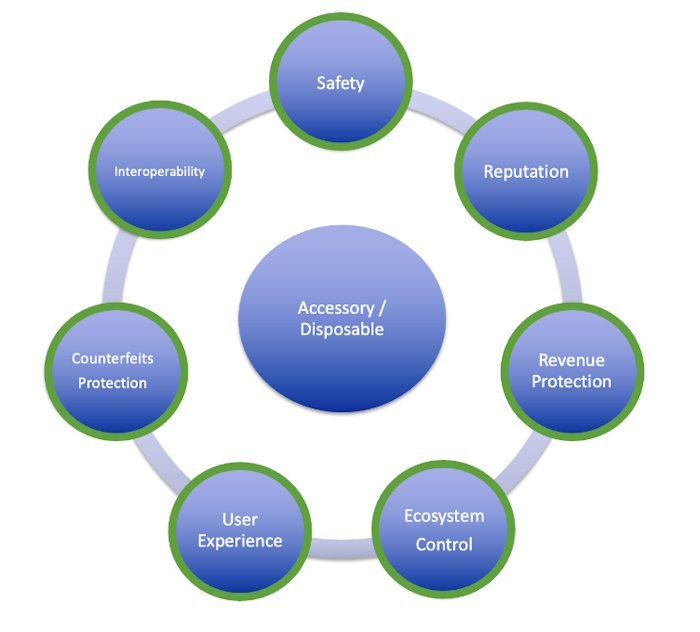
Figure 1 - Some of the many reasons why implementing crypto authentication is vital for many products (source Microchip)
Crypto authentication basics
Engineers can easily add a simple authentication approach to most electronics-based designs. Ideally, a contact-based method, say between a handheld power tool and a rechargeable battery pack, permits power for the device integrated into the power pack. The data transfer takes place across the power lines. Authentication could be performed by the manufacturer setting a password exchange between the handheld unit (host) and the battery pack (accessory). However, once an adversary or counterfeiter has obtained that password by analyzing the data transfer process, unauthorized copying of the accessory devices is straightforward. A more secure method is to place a secret code in a secure IC in the accessory and utilize a challenge-response protocol to determine authenticity. There are already established cryptographic algorithms that make this process safe, and these form the basis of two challenge-response cryptographic authentication methods: symmetric and asymmetric.
Figure 2 illustrates a symmetrical-based cryptographic challenge-response based on a secret key shared between the host device and the peripheral accessory. Initially, during product manufacturing and a process called provisioning, a secret key is created from a parent key together with a serial number of the end product. A hashing function then creates a derived key that is unique to each end product's peripheral accessory. Once used with customers, the host issues a random number challenge to the accessory. The anticipated response is a digital signature computed from the random number and the secret key. The host also runs the same process, and if the two results match, the accessory is deemed to be a genuine part. Secure-hash algorithms such as SHA-2 and SHA-3 are industry-standard methods issued and managed by the U.S. National Institute of Standards and Technology (NIST).
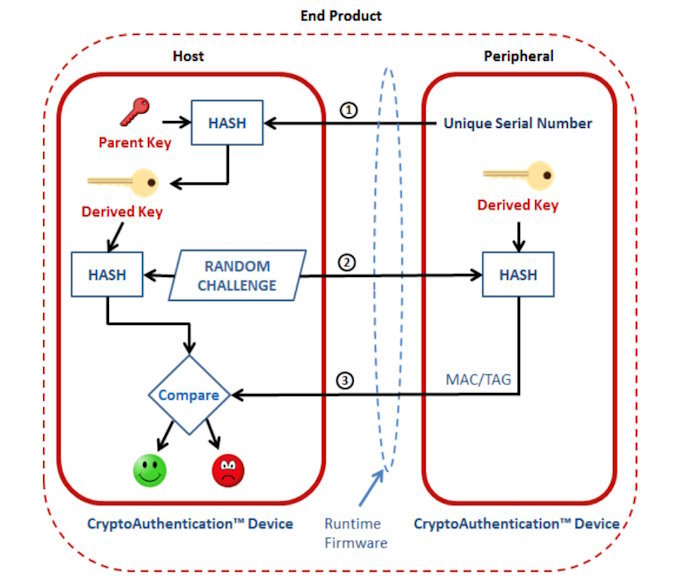
Figure 2 - Authenticating a peripheral accessory using a diversified secret key and a symmetrical cryptography (source Microchip)
An alternative method uses asymmetric cryptography which adds 3rd-party eco-system control capability. This method uses a pair of keys - public and private keys - commonly referred to as public key infrastructure (PKI) - see Figure 3. The private key resides in an authentication IC within the accessory, while the host uses the public key. As its name suggests, the public key may be disclosed without fear that it would compromise the security and authenticity of the accessory's private key.
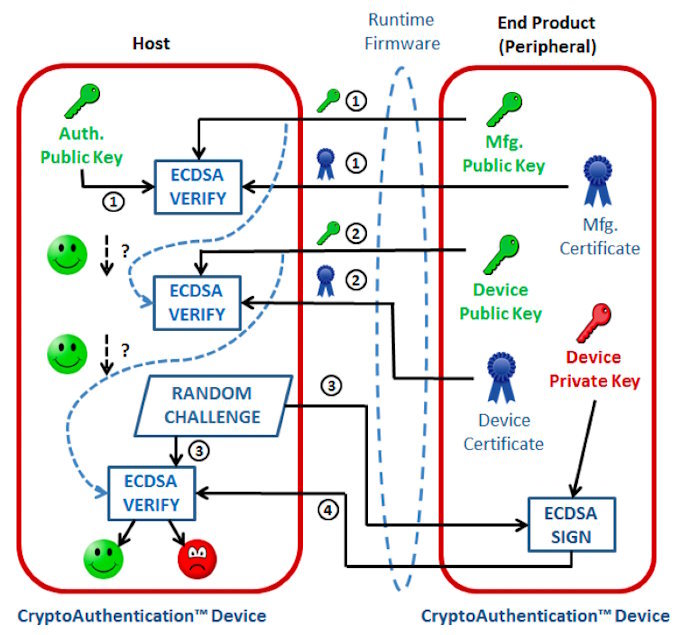
Figure 3 - A asymmetrical crypto authentication technique employs elliptic curve digital signature algorithms (ECDSA), digital certificates, public and private keys (source Microchip)
[Readers are directed to this Microchip resource to learn more about symmetrical and asymmetrical provisioning and the cryptographic authentication process.]
Implementing crypto authentication with Microchip's CryptoAuthenticationTM product line-up
Figure 4 showcases Microchip's line-up of secure authentication ICs, categorized by application. Examples include the ATECC608, the SHA 104, SHA 105, and SHA106 series, and the ECC204 and ECC206 portfolios.
Updated version:
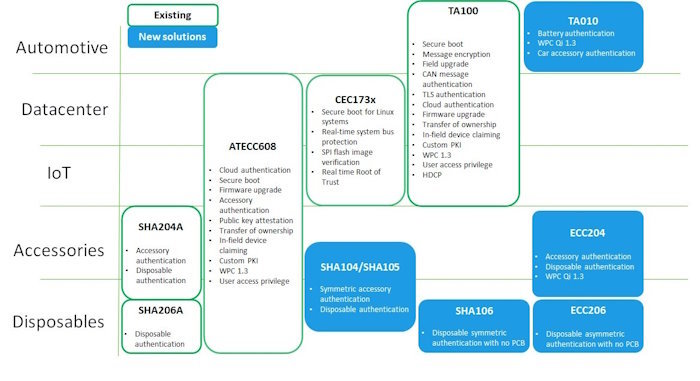
Figure 4 - The Microchip CryptoAuthentication IC line-up (source Microchip)
The ATECC608 is a pre-provisioned secure element IC designed to accommodate a wide range of use cases, from data centers to IoT applications. It securely stores secret, public and private keys and digital certificates. Communication with the host is achieved via the industry standard I2C serial bus or a single wire interface (SWI).
A growing requirement for crypto authentication comes from the healthcare and medical sectors. The increasing use of pouch-style medication packs, single-use diagnostic probes and disposable medical patches drives the need for item authentication. Not only does this reassure clinicians that the medication or accessory is from a legitimate source, but it also provides validation of the correct medication and dosage. It may also be required for medical regulatory compliance and clinical process. Other examples of space-constrained and cost-sensitive use cases include e-cigarettes, cosmetics and electronic e-bike cards.
For symmetrical crypto authentication, the SHA104 and SHA105 are members of Microchip's CryptoAuthentication portfolio, aimed at accessory and disposable use cases. They provide 128 bits of symmetrical cryptographic security. These ultra-compact ICs communicate over I2C or SWI and consume approximately 130 nA during sleep. They are available in 8-pin or 3-pin (power, SWI data and ground) package formats, making them particularly suitable for space-constrained applications. The ECC204 provides hardware support for ECDSA, SHA-256, and hash message authentication code (HMAC) for asymmetrical applications.
Figure 5 highlights Microchip's compact symmetrical and asymmetrical CryptoAuthentication ICs. With their low form factor packages, these devices can be used without a PCB, greatly simplifying their inclusion in various consumables and disposable accessories.
Updated version:
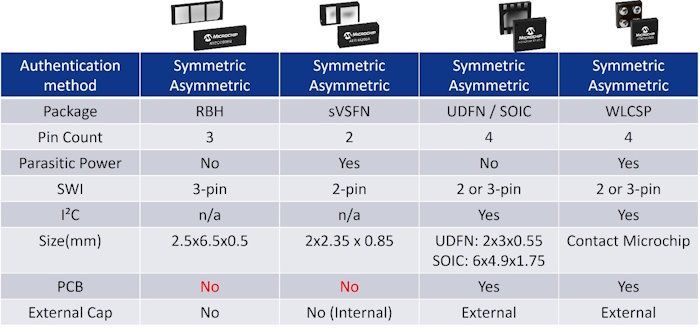
Figure 5 - CryptoAuthentication ICs suitable for small form factor, no PCB and parasitic power applications (source Microchip)
The SHA106 and ECC206 ICs reduce the pin count to just two pins, requiring a single wire interface and a ground connection. Figure 6 illustrates the simplicity of using a 2-pin crypto authentication IC where power is harvested from the SWI in an integrated capacitor sufficient to provide power for the authentication process. Also, without needing a PCB, the costs of implementing crypto authentication reduce while the number of use cases expands significantly.
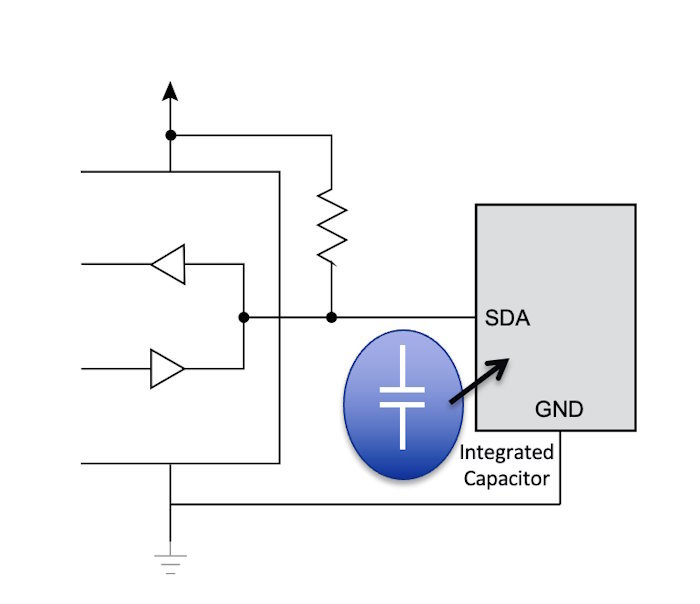
Figure 6 - The 2-pin Microchip SHA206 and ECC206 CryptoAuthentication ICs feature an internal capacitor to store parasitic energy that powers the device (source Microchip)
Crypto authentication surges forward
The availability of small form-factor, self-powered cryptographic ICs promises to push the authentication boundaries of disposable consumables and accessories. In addition to the CryptoAuthentication devices highlighted, Microchip provides evaluation boards, reference designs, and a comprehensive security platform design suite that covers everything from manufacturer provisioning to deployment.




